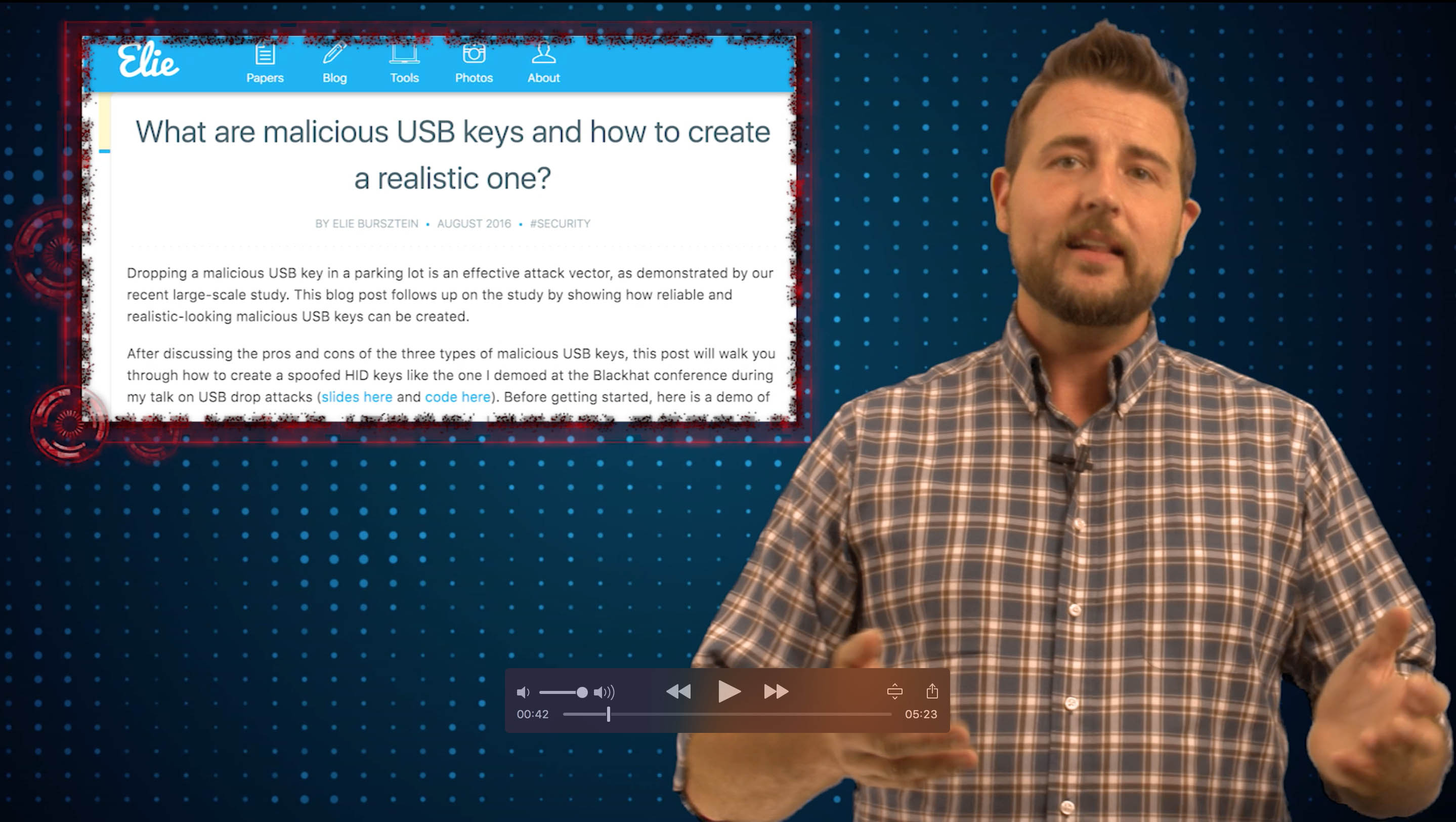
What are malicious usb keys and how to create a realistic one?
Par un écrivain mystérieux
Last updated 09 juillet 2024

This blog post shows how to create a reliable and realistic-looking malicious USB key that can be used in a drop attack.

What Is USB Killer Attack and How to Prevent It - IDStrong

How malware can infect your PC - Microsoft Support

How to make malicious Flash drives!

Cybersecurity Tip: Be Careful with That Free USB Stick
The Spies Who Loved You: Infected USB Drives to Steal Secrets

Curious people can't resist plugging in random flash drives

Infected USB Devices: How to Prevent USB-Based Attacks
Beware Random USB Sticks - Daily Security Byte - Secplicity

USB Flash Drives Are More Dangerous Than You Think - IEEE Spectrum

The Best Security Keys for Multi-Factor Authentication

This USB stick will fry your computer within seconds • Graham Cluley

Almost half of dropped USB sticks will get plugged in – Sophos News
Aegis Secure Key - USB 3.0 Flash Drive FAQ
Recommandé pour vous
 The 3 Best USB Flash Drives of 202414 Jul 2023
The 3 Best USB Flash Drives of 202414 Jul 2023 Flash Drive 128GB 3.0 USB Drive Photo Stick Thumb Drive USB Flash14 Jul 2023
Flash Drive 128GB 3.0 USB Drive Photo Stick Thumb Drive USB Flash14 Jul 2023 256GB Photo-Stick-for-iPhone, Apple MFi Cetified USB Flash Drive14 Jul 2023
256GB Photo-Stick-for-iPhone, Apple MFi Cetified USB Flash Drive14 Jul 2023 Personalised USB model Tradition, Custom USB sticks14 Jul 2023
Personalised USB model Tradition, Custom USB sticks14 Jul 2023 Orange USB Stick PNG Images & PSDs for Download14 Jul 2023
Orange USB Stick PNG Images & PSDs for Download14 Jul 2023 Usb Stick png images14 Jul 2023
Usb Stick png images14 Jul 2023 Usb Flash Drive 128gb Usb 3.0 Usb Stick Swivel Memory Stick High14 Jul 2023
Usb Flash Drive 128gb Usb 3.0 Usb Stick Swivel Memory Stick High14 Jul 2023 What To Do with That Found USB Stick14 Jul 2023
What To Do with That Found USB Stick14 Jul 2023 SanDisk Ultra Flair 32GB 3.0 USB Stick14 Jul 2023
SanDisk Ultra Flair 32GB 3.0 USB Stick14 Jul 2023 Fake Capacity USB Sticks - Dataquest14 Jul 2023
Fake Capacity USB Sticks - Dataquest14 Jul 2023
Tu pourrais aussi aimer
 Filament ABS, Diam 1.75mm, 1kg rouge14 Jul 2023
Filament ABS, Diam 1.75mm, 1kg rouge14 Jul 2023 FLO05068MI - Ensemble 3 entonnoirs petit moyen grand14 Jul 2023
FLO05068MI - Ensemble 3 entonnoirs petit moyen grand14 Jul 2023 Cartouche d'encre compatible Pomme T1295 Noir et couleurs (E129B/CLXL) - Toner Services14 Jul 2023
Cartouche d'encre compatible Pomme T1295 Noir et couleurs (E129B/CLXL) - Toner Services14 Jul 2023 Drap housse gaze de coton (160 cm) Gaïa Vert romarin - Linge de14 Jul 2023
Drap housse gaze de coton (160 cm) Gaïa Vert romarin - Linge de14 Jul 2023 Ração Sera Discus Granules Nature 420g Alimento para Discos14 Jul 2023
Ração Sera Discus Granules Nature 420g Alimento para Discos14 Jul 2023 Partial : 219 800 images, photos de stock, objets 3D et images vectorielles14 Jul 2023
Partial : 219 800 images, photos de stock, objets 3D et images vectorielles14 Jul 2023 SanDisk iXpand Flash Drive Go 64GB USB 3.0 Type-A to Apple Lightning for iPhone & iPad Black / Silver SDIX60N-064G-AN6NN - Best Buy14 Jul 2023
SanDisk iXpand Flash Drive Go 64GB USB 3.0 Type-A to Apple Lightning for iPhone & iPad Black / Silver SDIX60N-064G-AN6NN - Best Buy14 Jul 2023 Audio Technica LP60XBT Automatic Belt Drive Turntable with Bluetooth – TECH414 Jul 2023
Audio Technica LP60XBT Automatic Belt Drive Turntable with Bluetooth – TECH414 Jul 2023 Cravate Harry Potter Gryffindor BM14 Jul 2023
Cravate Harry Potter Gryffindor BM14 Jul 2023 AFYH Accessoires De Cheminée, Ventilateur De Cheminée, Poêle À Bois, Ventilateur De Poêle, Pas d'alimentation De La Batterie 4 Lames Smart Air Spiral À Induction Intelligente, : : Bricolage14 Jul 2023
AFYH Accessoires De Cheminée, Ventilateur De Cheminée, Poêle À Bois, Ventilateur De Poêle, Pas d'alimentation De La Batterie 4 Lames Smart Air Spiral À Induction Intelligente, : : Bricolage14 Jul 2023